TECH TALK: Net Neutrality goes nuclear

 ERIC’S TECH TALK
ERIC’S TECH TALK
by Eric Austin
Computer Technical Advisor
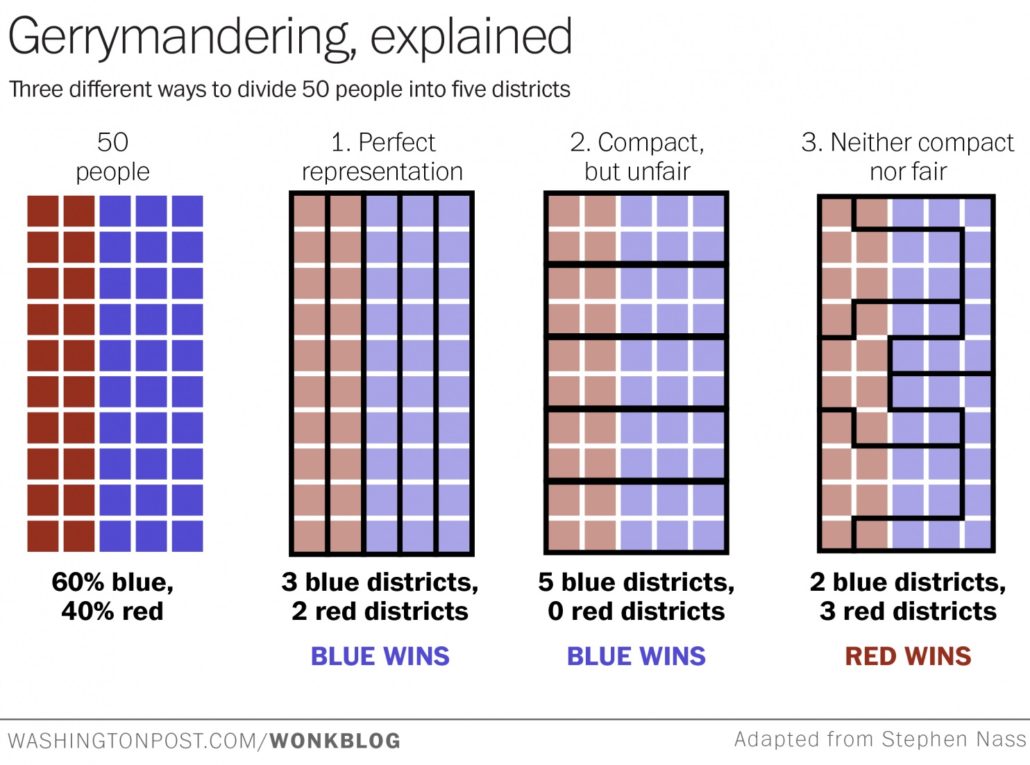
Do you like your cable TV service? I hope so, because your internet service is about to get a whole lot more like it.
On Thursday last week, the Federal Communications Commission (FCC), headed up by Trump appointee and former Verizon employee Ajit Pai, voted 3-2, along party lines, to repeal Obama-era rules that prevented internet providers from favoring some internet traffic over others.
You know how the cable company always puts the one channel you really want in a higher tier, forcing you to pay for the more expensive package even though you don’t like any of the other channels?
That’s right. Nickel-and-diming is coming to an internet service near you!
What does this really mean for you? I’m so glad you asked, but I’m afraid my answer will not make you happy.
It means that huge telecommunication companies like Comcast and TimeWarner now have the power to determine which internet services you have access to.
If you have a niche interest you pursue on the internet, you’re likely to be affected. Those websites with smaller audiences will have their bandwidth throttled unless you, the consumer, begin paying your Internet Service Provider (ISP) an extra fee.
That means you, Miniature Train Collector! That means you, Bass Fisherman! That means you, Foot-Fetish Fanatic!
It means pay-to-play is coming to the internet. When ISPs are allowed to favor some traffic over others, the Almighty Dollar will determine the winners and losers.
It means smaller newspapers like The Town Line, already suffering in a climate of falling ad revenue and competition from mega-sites like Buzzfeed and Facebook, will be forced to struggle even harder to find an audience.
Remember when chain super-stores like WalMart and Lowe’s forced out all the mom and pop stores? Remember when Starbucks and Subway took over Main Street?
That’s about to happen to the internet.
This move puts more control in the hands of mega-corporations – and in the hands of the men who own them. Do you want to choose your ISP based on where you fall on the political divide? What if Rupert Murdoch, owner of Fox News, bought Fairpoint or Spectrum? Which viewpoints do you think he would be likely to favor? Which websites would see their traffic throttled? What about George Soros, the billionaire liberal activist? No matter which side of the political divide you come down on, this is bad news for America.
In 2005, a little website called YouTube launched. It was competing against an internet mega-giant called Google Video. Two years later Google bought the website for $1.65 billion. Today, YouTube is one of the most popular websites on the internet.
That won’t happen in the future. Under the new rules, Google can simply use its greater capital to bribe ISPs to squash competitor traffic. YouTube would have died on the vine. In fact, that’s exactly what’s likely to happen to YouTube’s competitors now. Oh, the irony!
Twitter, YouTube, Facebook — none of these sites would be successes today without the level-playing field the internet has enjoyed during its first two decades of life.
So this is now the future of the internet. The barrier to innovation and success just became greater for the little guy. Is that really what the web needs?
These are dangerous days we live in, with freedom and democracy apparently assailed from all sides. The internet has been a beacon of hope in these troubled times, giving voice to the voiceless and leveling the playing field in a game that increasingly favors the powerful.
This decision by the FCC under Trump is a huge boon to the power of mega-corporations, telecommunications companies, and established monopolies, but it’s a flaming arrow to the heart of everyday, average Americans and future entrepreneurs. America will be the poorer because of it.
If there’s anything left of the revolutionary spirit that founded America, it lives on in the rebellious noise of the World Wide Web. Let’s not squash it in favor of giving more money and control to big corporations. America has had enough of that. Leave the internet alone!
Eric Austin is a writer and technical consultant living in China, Maine. He writes about technical and community issues and can be contacted at ericwaustin@gmail.com.





 Unlike your personal computer, a driverless car is a thinking machine. It must be capable of making moment-to-moment decisions that could have real life-or-death consequences.
Unlike your personal computer, a driverless car is a thinking machine. It must be capable of making moment-to-moment decisions that could have real life-or-death consequences.
 Instead of a few grainy pictures on the front page of the Evening Post, thousands of photos and live video got posted to the internet.
Instead of a few grainy pictures on the front page of the Evening Post, thousands of photos and live video got posted to the internet.