TECH TALK: The Internet – At War with Itself
 ERIC’S TECH TALK
ERIC’S TECH TALK
by Eric Austin
Computer Technical Advisor
There’s a war going on, although you might not be aware of it. It’s a war between the almighty dollar and the information superhighway.
I began my career in the early ‘90s, just as the internet-fueled tech boom was taking off. I’ve watched the internet grow from a tiny seed in the mind of Al Gore (ha ha) to the social and economic juggernaut that it is today.
But even from its very inception there were two competing ideas fighting to shape its future. One was an outgrowth of a cultural groupthink: the “hippie” movement of the internet, if you will. It’s an apt comparison, as the philosophy it inspired hearkens back to that optimistic era of peace and love.
This group believed the internet was a chance for humans to reinvent themselves. To escape the shackles of corporatism and Gordon Gekko-greed that had defined the previous decade of the 1980s.
The phrase “information wants to be free” defined this school of thought.
The “open-source” software movement, based on the idea of collaborative genius — that a group of unfettered minds could create something greater than any of its individual parts — gave birth to the Linux operating system, Firefox browser, VLC Media Player, GIMP and many other software programs. Each of us benefits from this movement whenever we download free software distributed under the GNU General Public Software License. And while it’s still only a sliver of the desktop market in comparison to Microsoft Windows, Linux dominates on mobile devices (56 percent) and powers more than 40 percent of the world’s web servers.
You can see the influence of this collaborative philosophy everywhere on the internet, and the world wide web is a better place because of it.
But there is another entity on the internet. A menacing, dark presence that wants to swallow up the hope and optimism of the free information movement. This force seeks to monetize and control the avenues of free access which the internet currently fosters. Rather than bettering society through collaborative social effort, this capitalist creature wants to conquer in the name of cold hard cash. It wants to turn the internet superhighway into a toll road.
This shadow over the internet is cast by ISPs, digital distribution giants and communication companies seeking to cement their dominance over their respective consumer markets.
The debate over Net Neutrality is the most recent battle to be waged in the war of $$ vs WWW. It promises to provide greater stability, consistency and service, but takes away freedom, ingenuity and the unexpected.
I’m here to tell you this is a war we need. It’s one of the good wars. This struggle is what keeps corporate greed on its toes. It leaves room for small start-ups to make an unexpected splash, and keeps established familiars from becoming complacent – yet provides the structure and efficiency that stimulates growth.
Without one we wouldn’t have great services like Netflix and Amazon. But without the other, great services like Netflix and Amazon never would have gotten the chance.
Net Neutrality must be retained because it levels the playing field. It doesn’t prevent bullies on the playground, but it makes sure everyone has a fighting chance.
Support Net Neutrality, not because it’s the right thing to do — even though it is. Support it because without the conflict it creates we wouldn’t have the dynamic technical environment that we’ve enjoyed for the last 20 years.
This is one time when conflict is good. Besides, it frustrates the corporate overlords.
Good. Keep them frustrated.
Get involved! Visit goFCCyourself.com and join almost 11 million other Americans who have left comments with the FCC in support of Net Neutrality.



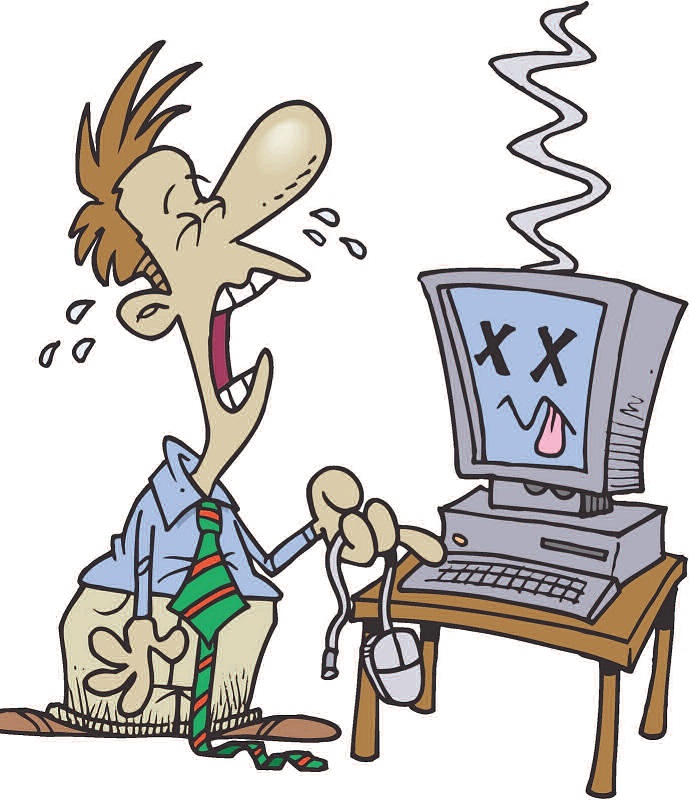
 And it got me thinking. Is there any law on the books requiring an Artificial Intelligence to tell you it is an artificial intelligence? After a bit of research, I found
And it got me thinking. Is there any law on the books requiring an Artificial Intelligence to tell you it is an artificial intelligence? After a bit of research, I found 
 One of the new ways kids have found to stay inside during beautiful summer days in Maine, is with a new activity called “binge-watching.” Essentially, binge-watching is the practice of watching multiple episodes of a single TV show in one sitting.
One of the new ways kids have found to stay inside during beautiful summer days in Maine, is with a new activity called “binge-watching.” Essentially, binge-watching is the practice of watching multiple episodes of a single TV show in one sitting. Each episode deals with a single cassette tape, which involves a revelation about how one of her fellow classmates has wronged her, leading to her ultimate decision to kill herself.
Each episode deals with a single cassette tape, which involves a revelation about how one of her fellow classmates has wronged her, leading to her ultimate decision to kill herself. That doesn’t sound like much fun, does it? Why would anyone want an Internet that works this way?
That doesn’t sound like much fun, does it? Why would anyone want an Internet that works this way? Certain other applications will also transfer data between the Internet and your computer, like games being played online, programs downloading updates, or certain programs that have specific network functions such as FTP programs for updating websites, or P2P (Peer-to-Peer) file-sharing applications for downloading large files.
Certain other applications will also transfer data between the Internet and your computer, like games being played online, programs downloading updates, or certain programs that have specific network functions such as FTP programs for updating websites, or P2P (Peer-to-Peer) file-sharing applications for downloading large files.
 A VPN service accepts your network communications, and then sends them back out to the Internet using its own IP Address in place of yours. In this way, none of your activities can be linked back to your personal computer. Instead, they would link back no further than your VPN server, which millions of other people also use.
A VPN service accepts your network communications, and then sends them back out to the Internet using its own IP Address in place of yours. In this way, none of your activities can be linked back to your personal computer. Instead, they would link back no further than your VPN server, which millions of other people also use. 2. Join the Conversation! Got a grievous grumble caught in your gullet? Unlike the paper, the website allows you to post your comments on every story! Just remember that we at The Town Line follow the BNBR (Be Nice, Be Respectful) policy, and any comments that breach this will not be approved!
2. Join the Conversation! Got a grievous grumble caught in your gullet? Unlike the paper, the website allows you to post your comments on every story! Just remember that we at The Town Line follow the BNBR (Be Nice, Be Respectful) policy, and any comments that breach this will not be approved! Remember when the most you had to remember was your ATM pin? Those days are gone, and now pretty much every website wants you to log in with a username and password. If you are like many people, you might use the same combination for multiple sites (except for those sites where somebody already took my username! Arrgghhh!).
Remember when the most you had to remember was your ATM pin? Those days are gone, and now pretty much every website wants you to log in with a username and password. If you are like many people, you might use the same combination for multiple sites (except for those sites where somebody already took my username! Arrgghhh!). There are a number of good ones available. Personally, I use
There are a number of good ones available. Personally, I use  Surprisingly, the most secure way to store your passwords may be the old-fashioned way: with paper and pen. Keep a notebook next to your computer and write each one down. Just don’t leave your notebook somewhere carelessly like an airport or restaurant!
Surprisingly, the most secure way to store your passwords may be the old-fashioned way: with paper and pen. Keep a notebook next to your computer and write each one down. Just don’t leave your notebook somewhere carelessly like an airport or restaurant! As a final piece of advice, and tying back to my headline, let me emphasize that not all accounts are created equal. If you have a Google or Microsoft account which ties all your other accounts together (the one where a password support request from other websites will be sent), give special care to the password you use for that account, and change it at lease every six months.
As a final piece of advice, and tying back to my headline, let me emphasize that not all accounts are created equal. If you have a Google or Microsoft account which ties all your other accounts together (the one where a password support request from other websites will be sent), give special care to the password you use for that account, and change it at lease every six months.